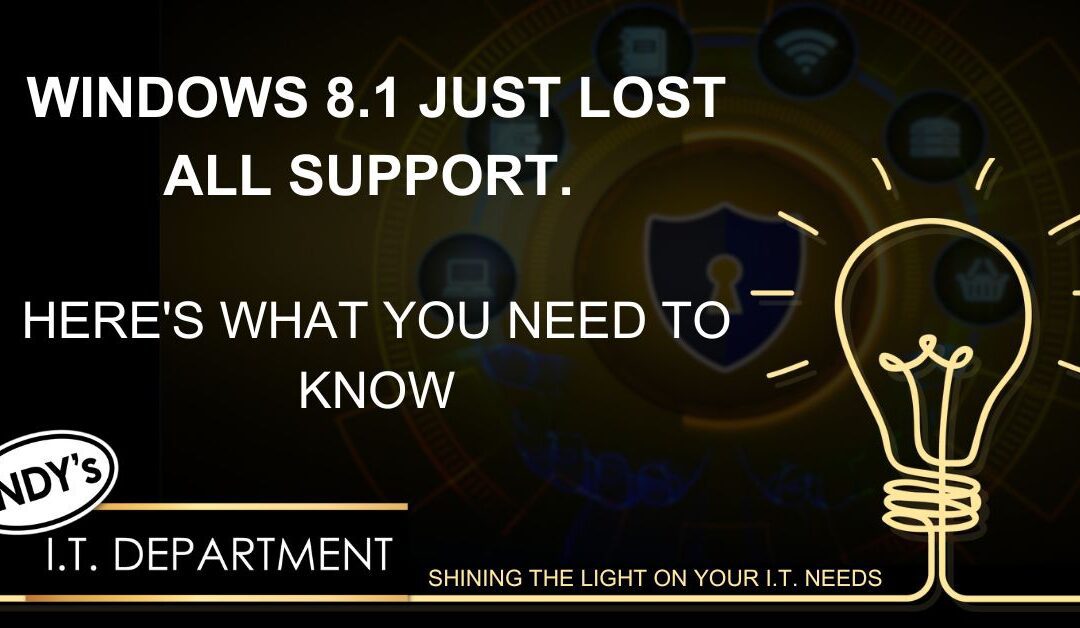
by Daniel Curry | Apr 30, 2023 | Cyber Security, Cybersecurity, Microsoft, New Technology
Companies both large and small share this one cybersecurity problem. They have computers that are still running older operating systems (OS). Staff might use these devices only occasionally. Or the company may be running customized software that won’t run on newer OS...

by Daniel Curry | Apr 25, 2023 | Cyber Security, Cybersecurity, New Technology
It’s a common theme. You begin seeing these amazing CGI images of your friends on Facebook or Instagram. You think, “How can I make one?” Filters and self portrait apps have come a long way and are becoming quite popular. You can now make yourself look like...

by Daniel Curry | Mar 30, 2021 | Ring Ring
Ring! Ring! Me: I.T. Department, this is Daniel. How can I help you? Caller: I can’t log into my computer. Me: OK. How can I help you? Caller: Help me log into my computer! Me: OK. Let’s back up a couple of steps. I’m Daniel. Who are you? Caller:...

by Daniel Curry | Feb 7, 2021 | Ring Ring
Ring! Ring! Me: I.T. Depar…. Caller: Hey, Dan? This is Terry. Me: Hello, Terry. What can I do for you, today? Terry: My wife just bought a new computer. From Amazon. It comes with McAfee Security or something like that. Do we even NEED an internet security...

by Shawna Barnes | Mar 21, 2020 | Ring Ring
Welcome to Part 2 of Data Protection and Recovery – When cheap is expensive Barry: I’m about to lose everything, aren’t I? Me: Maybe. Barry: This would be data recovery, right? Me: At this point, yes, it would be. Barry: Data recovery is expensive. Me: It...